Not getting noticed by recruiters?
Personalise & tailor resume for every job you apply
Visit any jobs page and click on magic cap button to generate a tailored resume from your regular resume
Use ChatGPT to customise your resume for every job that you apply to
Use AI to auto fill job forms
Ask for Referral for any job post
Adit Shah
Security Incident Manager
Education Overview
• northeastern university
• gujarat university
Companies Overview
• twilio
• rsa security
• massmutual
• oppenheimerfunds
• northeastern university
Experience Overview
10 Years
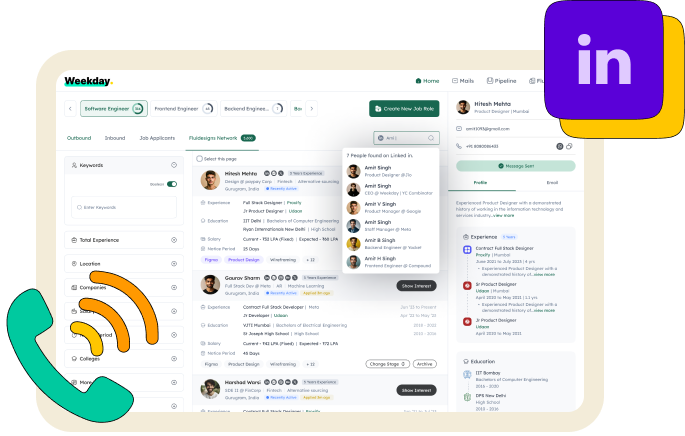
Find anyone’s contact
Experience
No data found
Skills
Boost your visibility and stand out to employers with referrals from your LinkedIn connections.
Contact Details
Email (Verified)
adiXXXXXXXXXXXXXXXXXXXXXomMobile Number
+91XXXXXXXXXXEducation
No data found
Frequently asked questions
Find anyone’s contact and let Weekday reach out to them on your behalf
Start hiring nowStop manually filling job applications. Use AI to auto-apply to jobs
Look for jobs now




